Title: Exploring UDP Programming: Concepts, Challenges, and Solutions
Introduction to UDP Programming
UDP (User Datagram Protocol) is a connectionless protocol used for transmitting datagrams over a network. Unlike TCP, UDP does not guarantee delivery, ordering, or errorchecking of packets. Despite its simplicity, UDP is widely used in various applications where realtime communication and low overhead are prioritized.
Key Concepts in UDP Programming
1.
Socket Programming
: UDP communication relies on sockets, which are endpoints for sending and receiving data. In programming, developers create UDP sockets to establish communication between different hosts.
2.
Connectionless Communication
: Unlike TCP, UDP is connectionless, meaning there is no establishment of a session between the sender and receiver. Each UDP packet is independent and can be sent without prior setup.
3.
Unreliable Delivery
: UDP does not guarantee packet delivery. Packets may arrive out of order, duplicate, or not at all. Therefore, applications built on UDP must handle packet loss and ordering if necessary.
4.
Low Overhead
: UDP has minimal overhead compared to TCP since it lacks features like error recovery and flow control. This makes it suitable for applications where speed is critical, such as realtime multimedia streaming and online gaming.
Challenges in UDP Programming
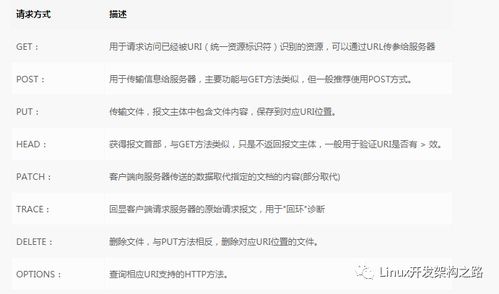
1.
Packet Loss
: Due to its unreliable nature, UDP may experience packet loss, especially in congested or unreliable networks. Developers must implement mechanisms to detect and recover from lost packets if required by the application.
2.
Packet Order
: Unlike TCP, UDP does not guarantee the order of packet delivery. Applications that rely on sequential data transmission must include sequence numbers or other mechanisms to reorder packets upon arrival.
3.
Congestion Control
: UDP does not have builtin congestion control mechanisms like TCP. Developers must design their applications to handle network congestion gracefully, possibly by implementing backoff strategies or rate limiting.
4.
Security Concerns
: UDP is susceptible to various security threats, including packet spoofing, amplification attacks, and denialofservice (DoS) attacks. Developers should implement security measures such as data validation and encryption to protect against these threats.
Solutions and Best Practices
1.
Error Handling
: Implement robust error handling mechanisms to detect and recover from packet loss. This may involve retransmitting lost packets or requesting retransmission from the sender.
2.
Packet Ordering
: Use sequence numbers or timestamps to reorder outoforder packets upon arrival. This ensures that the application receives data in the correct order, even in the presence of network delays or packet reordering.
3.
Congestion Management
: Design the application to handle network congestion gracefully. This may involve monitoring network conditions and adjusting the transmission rate dynamically to avoid overwhelming the network.
4.
Security Measures
: Implement data validation to ensure that incoming packets are legitimate and not spoofed or tampered with. Additionally, consider encrypting sensitive data to protect it from eavesdropping or manipulation.
Conclusion
UDP programming offers a lightweight and efficient means of communication for realtime applications. However, developers must be aware of its limitations and challenges, such as packet loss, unordered delivery, and security concerns. By understanding these concepts and implementing appropriate solutions and best practices, developers can harness the power of UDP while mitigating its drawbacks.
This concludes our exploration of UDP programming, covering key concepts, challenges, and solutions for building robust and reliable UDPbased applications.


